If you use Firefox version 52 or later and you have Lenovo/IBM IMM firmware 1.47 and later you'll notice that there is no progress after pressing the Login button in IMM web interface. This the latest flaw in what was once a great browser. The people over at Mozilla think they know what's best and decide to break stuff in the name of 'security'.
The Lenovo/IBM server may be any of the following:
- System x3100 M3, Type 4253, any model
- System x3250 M3, Type 4251, any model
- System x3250 M3, Type 4252, any model
- System x3250 M3, Type 4261, any model
- System x3500 M2, Type 7839, any model
- System x3500 M3, Type 7380, any model
- System x3550 M2, Type 4198, any model
- System x3550 M2, Type 7946, any model
- System x3550 M3, Type 4254, any model
- System x3550 M3, Type 7944, any model
- System x3650 M2, Type 4199, any model
- System x3650 M2, Type 7947, any model
- System x3650 M3, Type 4255, any model
- System x3650 M3, Type 5454, any model S
- System x3650 M3, Type 7945, any model
- System x3690 X5, Type 7147, any model
- System x3690 X5, Type 7148, any model
- System x3690 X5, Type 7149, any model
- System x3690 X5, Type 7192, any model
- System x3850 X5, Type 7143, any model
- System x3850 X5, Type 7145, any model
- System x3950 X5, Type 7143, any model
- System x3950 X5, Type 7145, any model
Lenvovo has a workaround, but that's hardly the proper solution. As described in the Lenovo support article, the root of the problem has to do with how your browser handles cookies. Upon further investigation it looks like this issue maybe goes a bit deeper than Mozilla.
There is an IETF draft draft-ietf-httpbis-cookie-alone-01, aptly named "Deprecate modification of 'secure' cookies from non-secure origins". It's unclear if it was indeed adopted, but the one linked says it expired. Regardless of whether or not it's an official standard, it looks like Mozilla decided to implement it. If you look closely it's got Google, Inc's name on it. Yes, Goolgle, another who responsible for breaking the Internet in the recent decades.
So it's a probable assumption that Chrome (and anything else based on it) will also have the same issue. However we're not going to acknowledged its legitimacy as a proper browser by continuing to talk about it.
Anyway, the correct way to resolve this issue is to fix the brokenness in the web browser by setting the config flag network.cookie.leave-secure-alone to false. This is done by going to about:config?filter=network.cookie.leave-secure-alone. Click the ominous button saying you promise to do no harm, then set the value as mentioned.
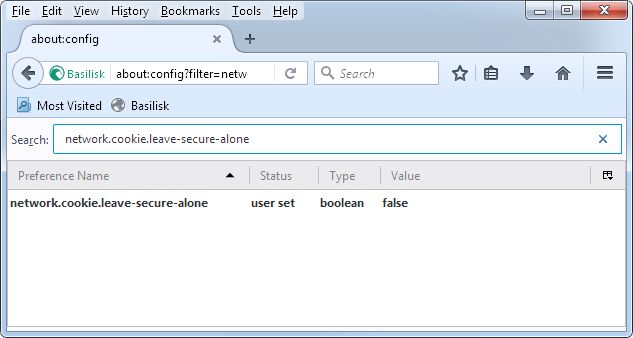
The change applies immediately, no need to restart
There is a chance Mozilla has removed this as a configurable option. If this is the case then there is only one thing to do. Download a new browser. A browser that you'll use to actually get work done. I suggest Basilisk. As of this writing Basilisk still has this as a configurable option.


.png)